What is OAuth:
It is a framework to facilitate delegated and controlled access on behalf of user. So basically, it is a protocol that allows a user to grant a given third-party web site or application access to the user’s protected resources, without necessarily revealing their long-term credentials or even their identity.
There are different flows in which OAuth delegates these accesses but before discussing this let us get acquainted with few of the terminologies.
- Resource Owner: Entity that can grant access to a protected resource. Typically, this is the end-user.
- Resource Server: Server hosting the protected resources. This is the API you want to access.
- Client: Application requesting access to a protected resource on behalf of the Resource Owner.
- Authorization Server: Server that authenticates the Resource Owner and issues access tokens after getting proper authorization. In this case, Auth0.
Pre-requisite – Client registration:
Before initiating the OAuth protocol flow for authorization, the client needs to register itself with the authorization server with following information-
- Client type: OAuth defines two client types, based on their ability to maintain the confidentiality of their client credentials – confidential and public.
- Redirection URI: Also called call-back URL to which user is redirected post authorization from auth server.
- Any other information required by the authorization server (e.g., application name, website, description, logo image, the acceptance of legal terms).
Client Authentication:
Post registration, Auth server issues the registered client
- Client identifier/Client_id: A unique string, encoded using the “application/x-www-form-urlencoded” encoding algorithm, representing the registration information provided by the client. It is public and unique identifier that represents the client.
- Client credential/Client_secret: A password, public/private key pair etc. It is used to authenticate the client when it raises request for Access token.
OAuth protocol endpoints:
The authorization process utilizes two authorization server endpoints-
- Authorization endpoint (auth server base uri + /authorizatin): used by the client to obtain authorization from the resource owner. The request contains a redirection url to which the auth server will redirect the user post successful resource-owner authentication along with an auth code.
- Token endpoint (auth server base uri + /token)- used by the client to exchange an authorization grant for an access token, typically with client authentication.
OAuth flows:
There are different ways, also called flows, using which OAuth provisions delegation of authorization. And this is governed by the term ‘grant types’. In OAuth, an authorization grant is an abstract term used to describe intermediate credentials that represent the
resource owner authorization. Several authorization grant types are defined to support a wide range of client types and user experiences as below-
1. Authorization code grant (grant_type=’code’):
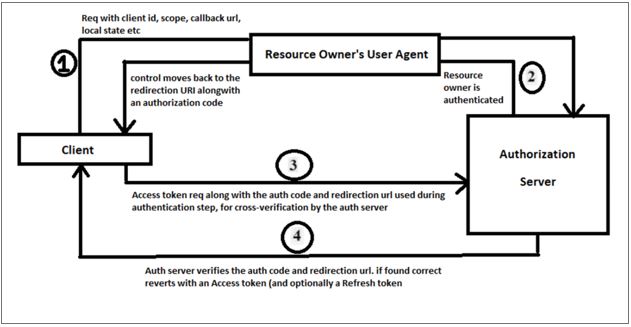
A few points to note about this flow-
- The exchange of authorization code is done through a front channel which is considered less secure, but the exchange of Access token usually happens through back channel. This also happens to be one of the benefits of this flow over others.
- Resource owner’s user agent is typically a web browser.
- Local state parameter: It is an opaque value used by the client to maintain state between the request and call-back. The authorization server includes this value when redirecting the user-agent back to the client. The parameter SHOULD be used for preventing cross-site request forgery
2. Implicit grant flow (grant_type=’token’):
This grant type differs from Authorization grant flow in skipping the step where Auth server sends Auth code to the client. It instead sends the Access token directly in the redirection URI fragment. The user-agent then requests web-hosted client resource which returns a web page, typically containing HTML and an embedded script capable of accessing the URI fragment retained by user-agent. User-agent then runs this script to extract the access token and return to the client.
3. Resource owner password credential grant (grant_type=’password’):
Here the access token is facilitated in 3 steps as below-
- The request owner provides the client with its username and password
- The client requests an access token from the authorization server’s token endpoint by including the credentials received from the resource owner. When making the request, the client authenticates
with the authorization server. - The authorization server authenticates the client and validates the resource owner credentials, and if valid, issues an access token.
4. Client Credentials Grant (grant_type=’client_credentials’):
The client can request an access token using only its client credentials (or other supported means of authentication) when the client is requesting access to the protected resources under its control. The client credentials grant type MUST only be used by confidential clients. It has following 2 steps.
- The client authenticates with the authorization server and requests an access token from the token endpoint.
- The authorization server authenticates the client, and if valid, issues an access token.
5. Extension grant:
The client uses an extension grant type by specifying the grant type using an absolute URI (defined by the authorization server) as the value of the “grant_type” parameter of the token endpoint, and by adding any additional parameters necessary. Extension grant types are there to support additional clients or to provide a bridge between OAuth and other trust frameworks. Let’s discuss one such grant-type below-
JWT Bearer token grant: This grant type is used when the client wants to receive access tokens without transmitting sensitive information such as the client secret. This can also be used with trusted clients to gain access to user resources without user authorization. Below are the steps to use this OAuth flow: –
- Create a JWT token by signing it using client’s private key
- Send request to token end point of authentication server. Ex-
POST /token.oauth2 HTTP/1.1
Host: https://www.googleapis.com/oauth2/v4
Content-Type: application/x-www-form-urlencoded
grant_type=urn:ietf:params:oauth:grant-type:jwt-bearer
&assertion=<JWT token created in step A>
3. Extract the access token from response

Your style is so unique in comparison to other folks I’ve read stuff from. Thank you for posting when you’ve got the opportunity, Guess I’ll just bookmark this web site.
There’s definately a great deal to know about this topic. I love all the points you made.
Excellent post. I am facing a few of these issues as well..
After looking over a number of the blog articles on your web site, I seriously like your way of writing a blog. I saved it to my bookmark webpage list and will be checking back soon. Take a look at my website too and tell me your opinion.
An intriguing discussion is worth comment. There’s no doubt that that you should publish more about this issue, it might not be a taboo matter but typically people don’t talk about such subjects. To the next! Best wishes!
Howdy very nice site!! Man .. Beautiful .. Wonderful .. I’ll bookmark your website and take the feeds additionally?I am happy to search out so many useful info right here in the submit, we’d like work out more techniques on this regard, thank you for sharing. . . . . .
Nice post. I was checking continuously this blog and I am impressed! Extremely useful information particularly the last part 🙂 I care for such information much. I was seeking this certain information for a long time. Thank you and best of luck.
I appreciate, cause I found exactly what I was looking for. You’ve ended my 4 day long hunt! God Bless you man. Have a nice day. Bye
WONDERFUL Post.thanks for share..more wait .. ?
I was wondering if you ever thought of changing the layout of your site? Its very well written; I love what youve got to say. But maybe you could a little more in the way of content so people could connect with it better. Youve got an awful lot of text for only having 1 or two images. Maybe you could space it out better?
Thank you for the auspicious writeup. It in fact was a amusement account it. Look advanced to far added agreeable from you! By the way, how could we communicate?
One other issue is that if you are in a predicament where you do not have a cosigner then you may actually want to try to make use of all of your financial aid options. You can get many funds and other scholarship grants that will provide you with funds to support with school expenses. Many thanks for the post.
How do I find out more?
Thanks for writing this article
That’s what i mean when i say that content is the king!
That’s what i mean when i say that content is the king!
I’ve to say you’ve been really helpful to me. Thank you!
Thank you for writing this post!
I always find your articles very helpful. Thank you!
Thank you for writing the article. I like the topic too.
Your articles are extremely beneficial to me. May I request more information?
It would be nice to know more about that. Your articles have always been helpful to me. Thank you!
I want to thank you for your assistance and this post. It’s been great.
You’ve been a great aid to me. You’re welcome!
Thank you for your excellent articles. May I ask for more information?
Thanks for the help
Thank you for writing such an excellent article. It helped me a lot and I love the topic.
Thank you for your post. I really enjoyed reading it, especially because it addressed my issue. It helped me a lot and I hope it will also help others.
Thank you for your post. I really enjoyed reading it, especially because it addressed my issue. It helped me a lot and I hope it will help others too.
Thanks for writing this article. I enjoy the topic too.
You’ve been a big help to me. Thank you!
I really appreciate your help
You’ve been a great help to me. Thank you!
I have to thank you for this article
Thank you for sharing this article with me. It helped me a lot and I love it.
Dude these articles were really helpful to me. Thanks a lot.
Thank you for writing this post!
You should write more articles like this, you really helped me and I love the subject.
May I request more information on the subject? All of your articles are extremely useful to me. Thank you!
It was really helpful to read an article like this one, because it helped me learn about the topic.
Thank you for writing this post. I like the subject too.
May I request more information on the subject? All of your articles are extremely useful to me. Thank you!
What are your articles about? Please tell me more.
Nice blog here! Also your site loads up very fast! What host are you using? Can I get your affiliate link to your host? I wish my website loaded up as quickly as yours lol
There is no doubt that your post was a big help to me. I really enjoyed reading it.
I want to thank you for your assistance and this post. It’s been great.
Thanks for your help and for posting this. It’s been great.
I’ve to say you’ve been really helpful to me. Thank you!
Your articles are extremely beneficial to me. May I request more information?
Thank you for your articles. They’re very helpful to me. May I ask you a question?
May I request that you elaborate on that? Your posts have been extremely helpful to me. Thank you!
Thank you for your excellent articles. May I ask for more information?
Thanks for writing this article
Thanks for posting. I really enjoyed reading it, especially because it addressed my issue. It helped me a lot and I hope it will help others too.
I always find your articles very helpful. Thank you!
Dude these articles have been really helpful to me. They really helped me out.
You’ve been terrific to me. Thank you!
Dude these articles were really helpful to me. Thanks a lot.
Thank you for posting this post. I found it extremely helpful because it explained what I was trying to say. I hope it can help others as well.
Please answer my question. How can i contact you regards this article?
May I request that you elaborate on that? Your posts have been extremely helpful to me. Thank you!
Thank you for writing such an excellent article, it helped me out a lot and I love studying this topic.
Thanks for the help
I envy your piece of work, appreciate it for all the useful blog posts.
It’s really a nice and helpful piece of info. I’m glad that you shared this useful info with us. Please keep us up to date like this. Thank you for sharing.
Great post. I was checking continuously this blog and I’m impressed!Extremely helpful information specially the last part 🙂 I care for such information a lot.I was looking for this particular info for a long time.Thank you and good luck.
These are in fact impressive ideas in regarding blogging.You have touched some nice factors here. Any way keep up wrinting.
Thanks for sharing, this is a fantastic blog article.Much thanks again. Will read on…
hi!,I love your writing very so much! share we be in contact extra about your article
on AOL? I need an expert in this space to unravel my
problem. May be that is you! Having a look ahead to see you.
Highly descriptive post, I enjoyed that a lot.
Will there be a part 2?
Hey there I am so delighted I found your site, I really found you by mistake, while I was researching on Aol for something else, Nonetheless
I am here now and would just like to say thank you for a incredible post and a all round enjoyable blog (I also love the theme/design), I don’t have time to go through
it all at the minute but I have book-marked it and also added your
RSS feeds, so when I have time I will be back to read a great deal more, Please do keep up the
great jo.
Nice post. I learn something totally new and challenging on sites I stumbleupon on a daily basis.
It’s always exciting to read content from other authors and use a
little something from their web sites.
After going over a handful of the blog posts on your website,
I really appreciate your way of blogging. I bookmarked it to my bookmark site list and will be checking back soon. Take a look at my
website as well and tell me how you feel.
Pretty nice post. I just stumbled upon your blog and wanted to
say that I have truly enjoyed surfing around your blog posts.
In any case I’ll be subscribing to your feed and I hope you
write again very soon!